802.11w Protected Management Frames (PMF)
802.11w Protected Management Frames
Why?
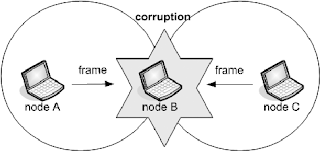
As you are aware that Management Frames are not encrypted in WLAN networks and this causes WLAN networks to be vulnerable to Denial of Service Attacks (DoS). Let us see a few of the Denial of Service attacks which Attackers can use to disrupt few or all of the users in a WLAN network.
DoS Attacks
Following frames can break the existing wireless connection (without PMF support) and will lead to Denial of Service attack.
Sending Deauth or Disassoc notification to AP
Sending (Re) Association request to AP.
Sending Auth frame to AP.
Sending Deauth or Disassoc notification to Station
Sending Channel switch announcement to Station.
How to solve the problem?
Once the 4 way Handshake is done, the AP and the STA have the PTK and GTK to encrypt data. The same keys can now be used to encrypt Management frames to provide a certain level of Protection against DoS Attacks.
Access Point and the Station both needs to have support for 802.11w for it to work. 802.11w can either be made "Optional" or "Mandatory" for clients.
With Optional, both 802.11w supported and non supported clients can connect to the AP, whereas,
With Mandatory, only 802.11w supported clients can connect to the AP.
Once 802.11w is enabled in the AP, it will advertise this in the RSNIE. There are 2 fields for PMF:
If 802.11w is supported by access point then "Management Frame Protection Capable" field is set.
If 802.11w is configured as mandatory then "Management Frame Protection Required" field is set.
Note: Since this information is in RSNIE, it makes it very clear that 802.11w is supported by only WPA2 clients (both Personal and Enterprise). Even Open Network does NOT support PMF
How is the Encryption done on Management Frames?
These are the mechanisms used to protect unicasts as well as multi-/broadcasts:
Unicast Management Frames:
- Use same PTK as for data frames
- Protect the previously unencrypted frame header via additional authentication data (AAD)
- Extended AES-CCM to handle unicast management frames
- Separate Receive Sequence Counter (RSC) for replay protection
Broad-/Multicasts Management Frames:
- Use new Integrity Group Temporal Key (IGTK) received during WPA key handshake
- New Algorithm: Broadcast Integrity Protocol (BIP)
- New Information Element: Management MIC IE with Sequence Number + Cryptographic Hash (AES128-CMAC based)
Here is an example for a protected and valid Disassociate with the protected flag set and a valid management sequence counter:

Great Attack Scenarios Explained:
This Blog will give you a better Understanding of how 802.11w can protect against attacks:


Did you hear there's a 12 word phrase you can speak to your crush... that will trigger intense emotions of love and impulsive attractiveness for you buried inside his chest?
ReplyDeleteThat's because hidden in these 12 words is a "secret signal" that fuels a man's instinct to love, worship and care for you with all his heart...
====> 12 Words Will Fuel A Man's Love Response
This instinct is so built-in to a man's genetics that it will drive him to work harder than before to build your relationship stronger.
In fact, triggering this all-powerful instinct is absolutely essential to achieving the best ever relationship with your man that the second you send your man one of the "Secret Signals"...
...You will soon notice him expose his mind and soul for you in a way he never expressed before and he'll distinguish you as the one and only woman in the universe who has ever truly understood him.
Another advantage of 802.11w is that it keeps your network from being deauthed by some jerk with a wifi module.
ReplyDelete