Wifi Roaming Techniques : Pre-Authentication, PMK Caching, OKC, Fast Transition - 11r
Wifi Roaming Techniques:
Why is Roaming Important:
Wifi is mostly used in devices which are mobile such as mobile phones, Laptops etc. User intend to use these device while moving from one place to another and it is expected that the devices are always connected to wifi and the user can continue his work seamlessly. It would not be desirable that wifi keeps disconnecting and connecting to other Access Point while the user is moving, there should be a way where in the client can remain connected to wifi network while it moves. This issue is addressed by Wifi Roaming.
Another important reason for Why Roaming is important is to understand that Wifi is now immensely used for Voice calls. We would not like to lose connectivity and have a crackling sound during a voice call. For this, the Roaming activity should be as soon as possible so that there is no significant disturbance to the user during the voice call.
A complete 802.1x Authentication process takes approximately more than 300 ms and voice packets are sent every 20 ms. If the voice packets aren't sent for such a long time then there will be significant crackle in the voice. Just imagine that an officer says "Don't Shoot" over a voice call and there is a crackle in the call and the other officer only gets to hear "Shoot". This crackle can cost a life, and as reliable test Engineers we need to make sure that the quality of wifi that we provide is reliable.
The whole idea to have roaming techniques is to avoid the EAP exchange and minimize the time to roam to new AP.
Before we start learning about different Roaming Techniques, let us learn about RSN IE that is found in Association Request, Reassociation Request, EAPOL keys.
This is one of the most important fields when dealing with roaming methods and different Security profiles.
Element ID : 48 for RSNIE
Length : Length of this RSN field
Version : 1
Group Cipher OUI and Group Cipher Type: This is to identify the group cipher and Type.
Pairwise Key Cipher Suite List: This is to identify the suite used for Pairwise Suite.
AuthKey Management count: To indicate the number of AKM supported
AuthKey Management Suite OUI: This is to indicate whether the Auth key management is PSK or 802.1x or FT or FT-PSK.
RSN capabilities: Different capabilities. Note that there is a flag to indicate Pre-Authentication.
PMKID count: Length of PMKID list
PMKID: This lists the PMKIDs cached within the device
Let us now learn few of the Roaming Techniques, its Pros and Cons as well.
Preauthentication:
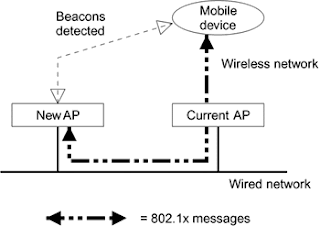
This technique works only for WPA2 Enterprise security. The client when finds a better AP than the current AP, it starts the 802.1x process with the New AP through the current AP instead of doing it on the Air after association process. In this way the process of 802.1x handshake is avoided on air and is done over the wired network. Now when the client roams to new AP, after the association it directly goes for 4-way handshake as the 802.1x exchange is already done via the current AP. This reduces the Roam time as 802.1x process is avoided to be done on air.
Pros and Cons:
Roam time is reduced as 802.1x authentication process is done prior to roam.
802.1x authentication is done everytime the client roams, this loads the Radius server. The situation gets worse when there are multiple clients all roaming continuously will load the Radius server and a lot of bandwidth gets wasted doing authentication many times.
PMK Caching:
In this roaming technique, Client does a 802.1x authentication with every AP it roams to and saves the PMK of all APs ( Clients usually have a limit of 32 PMK ). When client roams to the same AP again it had connected earlier, it does not do a 802.1x authentication again and instead, the client and AP uses the cached PMK to derive the PTK using 4-way handshake. In this way, by caching the PMK, 802.1x authentication is avoided and roam time is reduced.
Pros and Cons:
This technique does not load the radius server by caching the PMK.
This technique does not need a Wireless LAN controller and works with Autonomous AP.
There is a limit on the client as how many PMKs it can cache.
The client has to still do a complete dot1x authentication with all new APs it connects to.
OKC Caching:
The disadvantage of using PMK caching is that the client still needs to do complete 802.1x authentication with every AP. OKC on the other hand, uses Wireless LAN controller (WLC) to distribute the PMK with all the APs after the first 802.1x authentication done by the client.
This is one of the widely deployed Roaming technique before the deployment of FT.
Pros and Cons:
Works only with WLC based deployment.
Fast Transition:
Mobility Domain – A set of BSSs, within the same ESS, identified by a Mobility Domain
Identifier.
Fast BSS Transition – A STA movement from one BSS in one ESS to another BSS within the same ESS, that minimizes the amount of time that data connectivity is lost between STA and the DS.
Pairwise Master Key R0 (PMK-R0) – The key at the first level of the Fast BSS Transition key hierarchy
Pairwise Master Key R1 (PMK-R1) – A key at the second level of the Fast BSS Transition key hierarchy.
Pairwise Master Key R0 Key Holder (R0KH) – The component of RSNA key management of the Authenticator that is authorized to derive and hold the PMK-R0, derive the PMK-R1s, and distribute the PMK-R1s to the R1KHs.
Pairwise Master Key R0 Key Holder Identifier (R0KH-ID) – An identifier that names the holder of the PMK-R0 Key in the Authenticator
Pairwise Master Key R1 Key Holder (R1KH) – The component of RSNA key management of the Authenticator that receives a PMK-R1 from the R0KH, holds the PMK-R1, and derives the PTKs.
Pairwise Master Key R1 Key Holder Identifier (R1KH-ID) – An identifier that names the holder of a PMK-R1 key in the Authenticator.
Pairwise Master Key S0 Key Holder (S0KH) – The component of RSNA key management of the Supplicant that derives and holds the PMK-R0, derives the PMK-R1s, and provides the PMK- R1s to the S1KH.
Pairwise Master Key S0 Key Holder Identifier (S0KH-ID) – An identifier that names the holder of the PMK-R0 in the Supplicant.
Resource Information Container (RIC) – A sequence of Information Elements that include
resource request and response parameters.
Fast BSS Transition – A STA movement from one BSS in one ESS to another BSS within the same ESS, that minimizes the amount of time that data connectivity is lost between STA and the DS.
Pairwise Master Key R0 (PMK-R0) – The key at the first level of the Fast BSS Transition key hierarchy
Pairwise Master Key R1 (PMK-R1) – A key at the second level of the Fast BSS Transition key hierarchy.
Pairwise Master Key R0 Key Holder (R0KH) – The component of RSNA key management of the Authenticator that is authorized to derive and hold the PMK-R0, derive the PMK-R1s, and distribute the PMK-R1s to the R1KHs.
Pairwise Master Key R0 Key Holder Identifier (R0KH-ID) – An identifier that names the holder of the PMK-R0 Key in the Authenticator
Pairwise Master Key R1 Key Holder (R1KH) – The component of RSNA key management of the Authenticator that receives a PMK-R1 from the R0KH, holds the PMK-R1, and derives the PTKs.
Pairwise Master Key R1 Key Holder Identifier (R1KH-ID) – An identifier that names the holder of a PMK-R1 key in the Authenticator.
Pairwise Master Key S0 Key Holder (S0KH) – The component of RSNA key management of the Supplicant that derives and holds the PMK-R0, derives the PMK-R1s, and provides the PMK- R1s to the S1KH.
Pairwise Master Key S0 Key Holder Identifier (S0KH-ID) – An identifier that names the holder of the PMK-R0 in the Supplicant.
Pairwise Master Key S1 Key Holder (S1KH) – The component of RSNA key management in
the Supplicant that receives a PMK-R1 from the S0KH, holds the PMK-R1, and derives the
PTKs.
Pairwise Master Key S1 Key Holder Identifier (S1KH-ID) – An identifier that names the holder of the PMK-R1 in the Supplicant.
PMKR0Name – An identifier that names the PMK-R0.
PMKR1Name – An identifier that names a PMK-R1.
PTKName – An identifier that names the PTK.
Pairwise Master Key S1 Key Holder Identifier (S1KH-ID) – An identifier that names the holder of the PMK-R1 in the Supplicant.
PMKR0Name – An identifier that names the PMK-R0.
PMKR1Name – An identifier that names a PMK-R1.
PTKName – An identifier that names the PTK.
FT Key Architecture
The IEEE 802.11r amendment uses a three-tier key architecture. The Master Session Key (MSK) is
exported from the 802.1X/EAP authentication. When 802.1X/EAP is used, the MSK is sent in a
RADIUS attribute to the Authenticator (typically a controller) encrypted with the RADIUS shared secret.
In this way, the Supplicant and Authenticator will hold the MSK. When a Preshared Key (PSK) is used
for authentication, the PSK is used as the MSK by all stations in the ESS.
In a Split-MAC architecture, both the Supplicant and Authenticator use the MSK to derive the PMK-R0 and subsequently the PMK-R1 for each lightweight AP. The Authenticator (R0KH) uses a secure channel (not specified by the 802.11r amendment) to send each unique PMK-R1 key to the appropriate AP (R1KH). The Supplicant then performs an FT 4-Way Handshake with the initial AP to develop the PTKSA for that AP.
In a Split-MAC architecture, both the Supplicant and Authenticator use the MSK to derive the PMK-R0 and subsequently the PMK-R1 for each lightweight AP. The Authenticator (R0KH) uses a secure channel (not specified by the 802.11r amendment) to send each unique PMK-R1 key to the appropriate AP (R1KH). The Supplicant then performs an FT 4-Way Handshake with the initial AP to develop the PTKSA for that AP.
Fast BSS Transition (FT) Initial Mobility Domain Association
When a STA initially joins a mobility domain, it uses Open System Authentication and FT Association Request/Response frames (a 4-frame exchange). The 802.1X/EAP mutual authentication exchange between the Supplicant and AS and distribution of the MSK to the Authenticator by the AS follows. Once the PMK-R0 and PMK-R1 keys are derived at the R0KH device and unique PMK-R1 keys are distributed to R1KHs, then an FT 4-Way Handshake can be used to develop a PTKSA at the R1KH and S1KH. Once the PMK-R1 keys are distributed, there is no need to go through this initial process again within the same mobility domain.Over-the-Air Fast BSS Transition in an RSN
An AP must announce its specific support for over-the-air fast BSS transition in the Mobility Domain Information Element (MDIE) in Beacons, Probe Responses, and (Re)Association Responses. A Supplicant wishing to associate to an FT-enabled Authenticator must have matching MDIE information in its Authentication and (Re)Association Requests.When roaming within a mobility domain using over-the-air FT, STAs use FT Authentication Request/Response and FT Reassociation Request/Response frames as part of a 4-frame reassociation exchange. These four frames contain the appropriate information to build a PTKSA between the target (new) AP and the Supplicant. No 802.1X/EAP or 4-Way Handshake is necessary to unlock the 802.1X controlled port.
Notice that the ANonce, SNonce, and PMKR0Name
are exchanged during this frame exchange. The R1KH of the target AP uses the value of PMKR0Name
and other information in the frame to calculate PMKR1Name. If the target AP does not have the key
identified by PMKR1Name, it may retrieve that key from the R0KH identified by the STA. Upon
receiving a new PMK-R1 key for a STA, the target AP deletes the prior PMK-R1 SA and PTKSAs
derived from the prior PMK-R1 key. The STA and the target AP compute the PTK and PTKName using
the PMK-R1, PMKR1Name, ANonce, and SNonce.
Over-the-DS Fast BSS Transition in an RSN
When roaming within a mobility domain using over-the-DS FT, STAs use FT (Action Frame) Request/Response and FT Reassociation Request/Response frames as part of a 4-frame reassociation exchange. These four frames contain the appropriate information to build a PTKSA between the target (new) AP and the Supplicant. No 802.1X/EAP or 4-Way Handshake is necessary to unlock the 802.1X controlled port.Notice that the optional Resource Request protocol requires two additional frames: FT Authentication Confirm and FT Authentication ACK.
IEEE 802.11r Fast BSS Transition Summary
Keep in mind that in an FT Initial Mobility Domain Association, an FT 4-Way Handshake is used to develop a PTKSA between a Supplicant and Authenticator, but thereafter FT Protocols (over-the-air or over-the-DS) are used in place of the FT 4-Way Handshake. The FT Protocol exchanges are used to swap information between the Supplicant and Authenticator for the purpose of developing a fresh PTKSA for each target AP. Frame exchanges vary slightly based on whether over-the-air or over-the-DS is used and whether Resource Requests are necessary, but the results are still the same: a fast, fresh PTK.References : https://www.cwnp.com/uploads/802-11_rsn_ft.pdf









please provide wireshark sniffer captures also for the reference
ReplyDelete